Why Incident Governance is Critical for Utilities — And How One Risk Manager Got It Right
Why Incident Response and Crisis Management Belong to the CISO
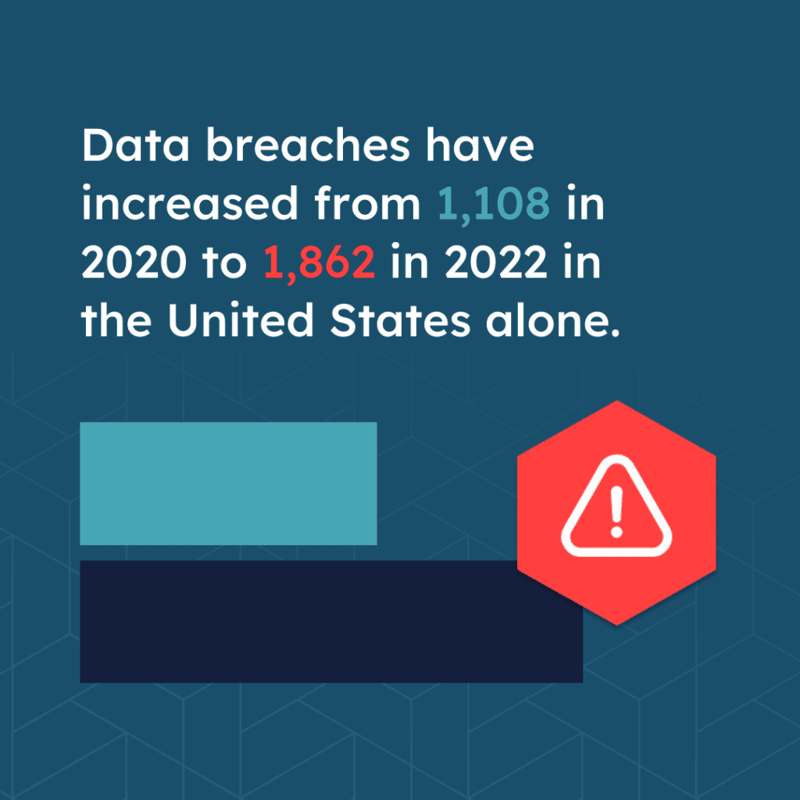
Incident response and crisis management is mission critical as data breaches, natural disasters, and other unforeseen events are becoming increasingly common. Data breaches have increased from 1,108 in 2020 to 1,862 in 2022 in the United States alone. Looking back further, in 2015, there were only 785 data breaches.
Natural disasters may also be more frequent in specific areas, and the COVID-19 pandemic highlighted the importance of being prepared for unforeseen events.
How can organizations address emerging incidents that threaten business continuity? Crisis management and incident management best practices aim to keep organizations ready to respond to any disruptive event.
The Chief Information Security Officer (CISO) is generally responsible for incident response and crisis management programs.
Other roles, such as CTOs and CIOs, take a different approach and have other responsibilities that are related to security, but CISOs take charge of preventing, mitigating, and responding to incidents at an organization-wide level.
Why is this role typically in charge of these critical programs? For CISOs reading this blog, we’ll offer up tips to help you optimize your incident response and crisis management programs.
Understanding Incident Response and Crisis Management
Incident response and crisis management are two critical components of an organization’s overall risk management strategy. While incident response focuses on the technical aspects of managing a security event, crisis management takes a broader perspective, addressing operational and communicative challenges. Together, they form a robust framework that is essential for minimizing the impact of a crisis, maintaining stakeholder trust, and protecting the organization’s reputation.
Incident response involves a systematic approach to identifying, containing, eradicating, and recovering from security incidents. It requires a well-coordinated effort among various teams to ensure that technical issues are swiftly addressed to prevent further damage. On the other hand, crisis management encompasses the strategic planning and execution needed to handle the broader implications of a crisis, including business operations and crisis communications.
A comprehensive incident response and crisis management framework enables organizations to respond effectively to any disruptive event. By integrating these functions, businesses can ensure a cohesive and efficient response, ultimately safeguarding their operations and reputation.
Why CISO's Own Incident Response
CISOs take charge of crisis management and incident response from a high-level view to prevent breaches and minimize the impact of a crisis. So, let’s explore why CISOs typically own this critical responsibility.
Expertise in Threats, Vulnerabilities, and Mitigation Strategies
CISOs generally reach their position due to extensive experience working in cybersecurity. On top of formal training, they’ve likely worked in the industry in various roles to gain direct experience evaluating, mitigating, and responding to various threats.
This expertise allows them to take an informed, high-level view of information security to manage risk evaluation and mitigation strategies. They’ll also be able to guide the development of crisis management and incident response due to their expertise and holistic view of the organization.
Manage Budget and Resource Allocation
Like other C-suite roles, CISOs must work within defined budgets and allocate resources to achieve stated goals effectively. Failing to meet these goals can spell disaster for infosec, as a single incident that isn’t properly responded to can inflict severe financial and reputational damage.
As such, CISOs need to find cost-effective ways to mitigate risks while also developing robust crisis management plans to respond to any of these risks if they become reality. Having the right people and systems in place, alongside robust incident response plans, is business critical.
Provide Cross-Functional Leadership
Even though CISOs work closely with IT, they aren’t the CTOs. Instead, a CISO works throughout the organization to ensure the holistic security of the entire enterprise’s digital assets.
As a result, they’re able to provide leadership throughout departments not usually associated with security. On the prevention side, this includes employee training in departments such as sales and customer service that are vulnerable to social engineering or phishing attacks.
The CISO can communicate how other departments should proceed if an incident occurs. Incident response plans specific to the given scenario will likely include these details, allowing managers of specific teams to provide effective guidance about how to proceed or interact with the public.
Align Efforts with Business Objectives
Being in the C-suite means the CISO is well aware of overall business objectives and likely contributes to defining them. From there, CISOs can guide infosec efforts, including crisis management and business continuity planning, focusing on current objectives.
As a cross-functional role with expertise in infosec, CISOs are able to make sure all crisis management programs and incident response plans focus on what matters most to the business. While a CTO accomplishes this strictly within the realm of IT, a CISO takes an all-encompassing approach.
The Incident Response Lifecycle
The incident response lifecycle is a strategic framework that embodies principles of preparedness, agility, and resilience. It involves a combination of people, processes, and technology working together to manage security incidents effectively. The lifecycle includes several key phases: identification, containment, eradication, and recovery.
During the identification phase, the goal is to detect and understand the nature of the incident. This involves monitoring systems and networks for signs of unusual activity. Once an incident is identified, the containment phase focuses on limiting its spread and impact. This may involve isolating affected systems or networks to prevent further damage.
The eradication phase aims to remove the root cause of the incident, such as eliminating malware or closing security vulnerabilities. Finally, the recovery phase involves restoring normal operations and ensuring that systems are secure and fully functional.
Effective incident response requires ongoing monitoring, evaluation, and improvement. By continuously refining the incident response process, organizations can enhance their ability to respond to future incidents more effectively, ensuring a resilient and agile approach to security.
Crisis Management Fundamentals
Crisis management is a critical function that helps organizations respond to and recover from unexpected events. It involves identifying potential risks, developing contingency plans, and training employees on crisis management procedures. A proactive approach is essential for effective crisis management, ensuring that organizations are prepared to handle any crisis that may arise.
Identifying potential risks is the first step in crisis management. This involves assessing various scenarios that could disrupt business operations, from natural disasters to cyber attacks. Once potential risks are identified, organizations must develop contingency plans that outline the steps to be taken in response to different types of crises.
Training employees on crisis management procedures is also crucial. This ensures that everyone knows their roles and responsibilities during a crisis, enabling a coordinated and efficient response. Regularly updating and testing crisis management plans is essential to ensure they remain effective and relevant in an evolving threat landscape.
By adopting a proactive approach to crisis management, organizations can enhance their resilience and ensure a successful crisis response, minimizing the impact on business operations and maintaining stakeholder trust.
CISOs Lead the Team During an Active Crisis Management
One critical responsibility of CISOs is to take charge of incident responses during an active incident. A well-prepared incident response team is crucial for effective management during an active incident. While preparation before an incident is necessary, having the right leader in place when one occurs is of the utmost importance.
Any business affecting an incident will create stress and tension, and these intensities can affect decision-making, making responses less effective. Ideally, the CISO will have the experience and expertise necessary to maintain a collected mindset and lead response and recovery efforts.
Additionally, having an already-appointed leader during a crisis can go far in aiding recovery efforts. Everyone involved in recovery efforts will already know who’s taking the lead. The CISO also steers efforts to the highest priority tasks and avoids the common pitfalls of diving too deeply into other aspects that do not pertain to incident responses.
For example, root cause analyses often seem necessary but often are not related to immediate response. CISOs help keep everyone focused on business continuity, saving other areas of concern for post-incident review.

CISOs – here are some tips to help you optimize your IR and crisis management efforts:
Overseeing Post-Incident Review
A critical component of crisis management and response is post-incident review. The overall goal of this process is to fully understand the cause of the issue, how it was responded to, and what changes can be made for stronger mitigation or faster resolution.
-
Establishing the scope: CISOs often begin post-incident review by defining what will be reviewed during evaluation. Reviewing incidents can often lead to far-reaching conversations that distract from honing in on finding what went wrong, what was great, and how to improve in the future. CISOs dictate the scope and keep everyone focused. And as a CISO, you’ll help everyone work together and operate under a single pane of glass.
-
Root cause analysis and overall lessons learned: Fully understanding what enabled the crisis is vital, especially for cyber attacks. From there, changes can be made to create more resilient defenses. Other crises, such as natural disasters, may have a clearer cause, but honing in on how those disasters affected the business must also be understood. CISOs will then be prepared to resolve incidents faster in the future and optimize related processes.
-
Implement corrective action: How can the company prevent another similar crisis from occurring? Or better respond if it does? The ultimate goal of post-incident review is to identify what can be done to prevent it or enhance response plans. Keeping this focus in front of mind is a core component of a CISO’s involvement in the process. Understanding these disasters and recovering faster from them will help create a faster path to resolution.
Technology and Tools for Enhancing Response and Management
Technology and tools play a crucial role in enhancing incident response and crisis management. They help organizations detect, respond to, and recover from incidents more effectively, leveraging advanced capabilities such as artificial intelligence, machine learning, and automation software.
Artificial intelligence and machine learning can analyze vast amounts of data to identify patterns and anomalies that may indicate a security incident. These technologies enable faster detection and more accurate identification of threats, allowing for a quicker and more effective response.
Automation software can streamline various aspects of incident response and crisis management, from initial detection to containment and recovery. By automating repetitive tasks, organizations can free up valuable resources and ensure a more efficient response to incidents.
These technologies and tools not only enhance the technical aspects of incident response but also support broader crisis management efforts. For example, communication platforms can facilitate real-time collaboration and information sharing among crisis managers, ensuring a coordinated and effective response.
By leveraging advanced technologies and tools, organizations can improve their incident response and crisis management capabilities, ensuring they are well-prepared to handle any crisis that may arise.
Is Your Company Ready for Its Next Crises?
Business-impacting incidents are increasingly frequent, including data breaches and natural disasters requiring rapid responses. Failure to respond can increase the damage caused by the incident and harm business continuity.
ShadowHQ equips your teams with a secure command center to ensure ongoing communication and collaboration, so your business can get back up and running. Our goal is to enable your teams to be prepared for any scenario that may come your way.
How ready is your business to rapidly respond to crises? We’ve put together a disaster readiness checklist to help you gauge existing initiatives and then implement changes to become more resilient. See if you’re prepared today.


.png?width=600&height=331&name=Image%20(1).png)