Building an Effective Data Breach Response Team for Your Organization
Understanding Data Breaches
A data breach is a security incident that results in the unauthorized disclosure, theft, or compromise of sensitive data. This can include protected health information, financial data, personally identifiable information, or other confidential data. Data breaches can occur due to various reasons, including insider threats, phishing attacks, malware, ransomware, or physical theft of devices. The consequences of a data breach can be severe, including financial losses, reputational damage, and legal liabilities.
Data breaches have become exceedingly common, and businesses cannot afford to assume that bad actors are not targeting them. Identity theft is one of the common causes of cyber threats that can lead to data breaches, alongside other issues such as insider leaks and human error.
And the numbers don’t lie. An Identity Defined Security Alliance report revealed that 90% of organizations with over 1,000 employees experienced at least one identity-related security incident within 12 months.
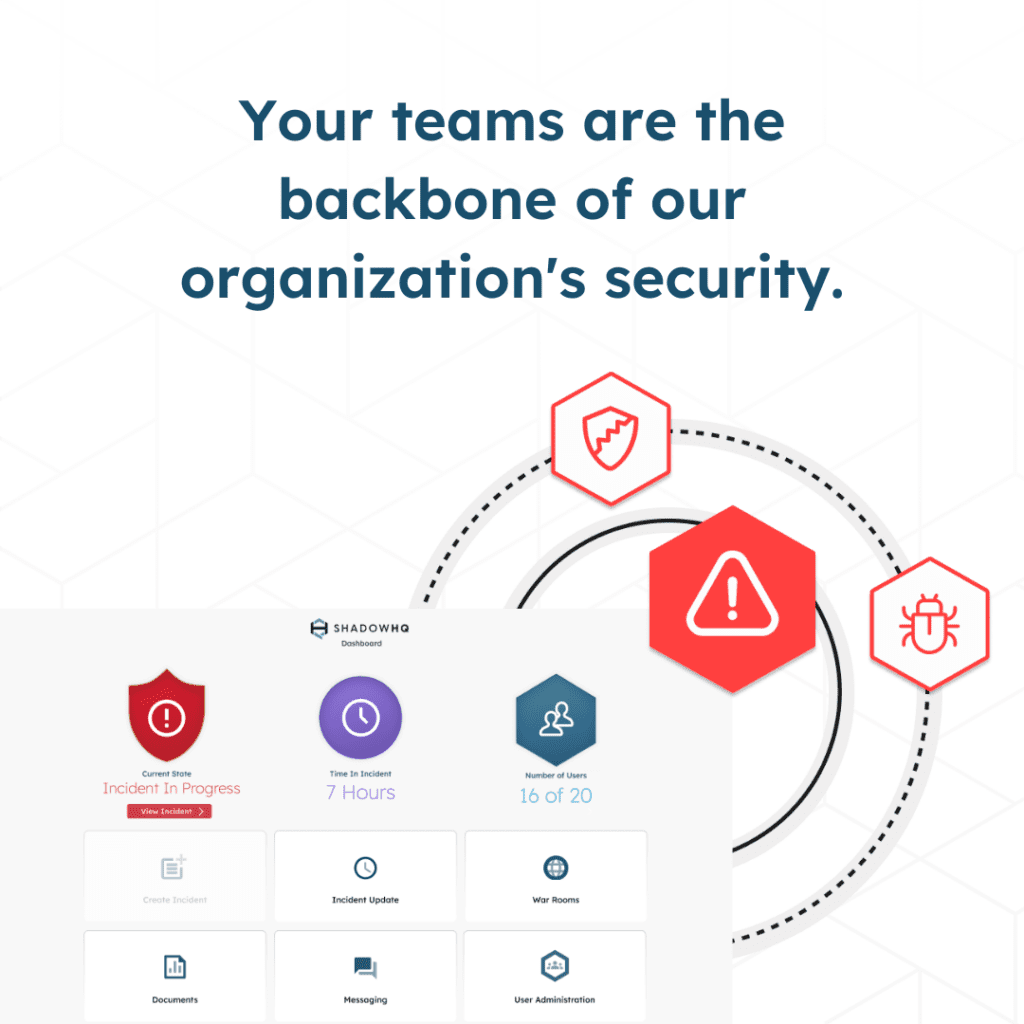
What’s clear: it’s not a matter of if, but when. Cyber resiliency is all about being prepared to manage an event quickly, limit damage, and get back to business as usual fast.
Preparing, practicing, and refining incident response plans helps your teams be ready to respond to an attack. A rapid response can minimize the impact of a successful breach, saving time, maintaining compliance standing, and protecting sensitive data.
So, let’s break down how your teams should respond to a breach so you can start preparing ahead of time.
How Will Your Teams Handle a Data Breach Response?
Responding effectively to a data breach is crucial for mitigating damage, maintaining trust, and complying with regulatory requirements.
Today, the incident response lifecycle includes:
Identify
Protect
Detect
Manage the attack surface
Recover and learn
Let’s explore a structured approach for what your team should do during a data breach.
Identifying a Threat
Responding to a breach begins by knowing when one occurs. This means developing an organizational understanding of cybersecurity risk to your systems, assets, data, and capabilities. Start by mapping out your organization’s risk profile and knowing how to properly assess this risk on an ongoing basis.
Implement Protection
Next, you’ll need to have a thorough understanding of the safeguards you’ve developed and implemented. These should be supported by internal controls and training exercises to build familiarity.
By doing this, you can establish the protective processes and procedures needed to keep your organization safe. More importantly, you can implement preventive measures and the right technologies needed to support these processes. For example, how and where will communications happen during a crisis if the core systems are down? You’ll need an out-of-band solution to keep the lines of communication open.
Detecting a Threat
It’s important to constantly monitor systems for signs of unauthorized access or unusual activities that may indicate a breach. And once detected, having the right teams in place to identify the breach’s source, the data involved, and the extent of the damage.
Detection and identification are crucial for effective containment and minimizing damage. The right platforms and processes must be in place to enable a rapid response to the incident and inform remediation efforts.
You’ll also need to ensure your incident response capabilities are well-defined. This will help enhance situational awareness and streamline implementing and following risk mitigation strategies.
Managing the Attack Surface
Managing the attack surface requires having the right safeguards in place to enable the ongoing delivery of services. Start by ensuring you have the right stakeholders involved and that anyone who’s part of the response can access relevant playbooks and business continuity files.
Next, activate your crisis communication tools to keep your response coordinated. Apply any incident analysis and mitigation processes that you have to gain a better understanding of the threat, current attack surface, and impacted systems.
Once identified, the breach must be contained. For short-term containment, isolate affected systems to prevent further data loss. This may involve disconnecting infected machines, changing passwords, or temporarily shutting down specific network segments.
In the long term, assess and secure vulnerabilities that enabled the breach to ensure they cannot be exploited again. Proper containment minimizes damage, maintains data integrity, and sets the stage for thorough remediation and recovery.
Recover & Learn
With the breach contained, it’s time to start the recovery process.
Be sure to review and execute your operational resiliency strategy. You should also review and apply any lessons learned. Additionally, look into where you can improve existing processes.
Gather and secure detailed logs, access records, and other evidence that might aid a forensic investigation. Assess the breach’s scope by identifying the compromised data and evaluating the potential consequences for the organization and affected individuals.
A thorough assessment and investigation provide insights into the root cause, enabling informed decisions for fast remediation and future prevention.
The goal of this stage is to implement and augment your recovery planning to better support future responses and enable the continuous improvement of your recovery capabilities.
Notification
Review legal and regulatory requirements to determine who needs to be notified, such as affected individuals, regulators, and partners, and adhere to the required timeframe. Ideally, this process will be handled during incident response planning so teams can easily refer to guidance during an active incident.
Communicate effectively with all stakeholders, including customers, employees, and partners, providing clear, transparent, factual information about the incident. Share details about what occurred, the data involved, and the steps being taken in response. Timely and accurate notification helps maintain trust and ensures compliance with legal obligations.
Remediation
Apply software updates, revise security policies, or enhance physical security measures to address the vulnerabilities that led to the breach. Use insights from the incident to strengthen security protocols and systems.
Explore opportunities to implement additional measures like multi-factor authentication, enhanced encryption, and improved access controls to bolster defense mechanisms. Remediation resolves current issues and prepares the organization to withstand future cyber threats better.
External Assistance
If the breach is complex or has significant legal implications, engage external cybersecurity experts or legal advisors. Their expertise can guide effective response and compliance.
Additionally, they cooperate with law enforcement in criminal activity cases to support their investigation and potentially bring perpetrators to justice. Collaborating with external partners ensures comprehensive incident handling and strengthens the overall security posture.
Building a Data Breach Response Team
A data breach response team, also known as an incident response team, is a critical component of an organization’s data breach response plan. The team should consist of individuals with diverse skill sets and expertise, including information security, legal, communications, and IT. The team’s primary responsibility is to respond to data breaches in a timely and effective manner, minimizing the impact of the breach and protecting the organization’s reputation.
Preparing for a Data Breach
Preparing for a data breach involves several steps, including:
Conducting a risk assessment to identify potential vulnerabilities and threats.
Developing a data breach response plan that outlines the steps to take in the event of a breach.
Establishing an incident response team and defining their roles and responsibilities.
Providing training and awareness to employees on data breach prevention and response.
Implementing security measures, such as encryption, firewalls, and access controls, to protect sensitive data.
Responding to a Data Breach
Responding to a data breach requires a swift and coordinated effort from the incident response team. The response should include:
Containment: Isolating the affected systems and data to prevent further unauthorized access.
Eradication: Removing the root cause of the breach, such as malware or unauthorized access.
Recovery: Restoring affected systems and data to a known good state.
Notification: Notifying affected parties, including individuals, organizations, and regulatory bodies, as required by law.
Post-incident activities: Conducting a thorough investigation, reviewing the incident response plan, and implementing changes to prevent similar breaches in the future.
Containment and Eradication
Containment and eradication are critical steps in responding to a data breach. Containment involves isolating the affected systems and data to prevent further unauthorized access. Eradication involves removing the root cause of the breach, such as malware or unauthorized access. These steps should be taken as quickly as possible to minimize the impact of the breach and prevent further damage.
Post-Incident Response Processes
While some of the above steps occur during or after an incident, other practices only occur after the incident has been eradicated and recovery is underway. So, let’s explore these post-incident processes that aim to prepare teams for a better response in the future.
Review and Learn
Conduct a post-incident review to analyze how the breach occurred and how the response was handled. Identify strengths and weaknesses in the response strategy, looking for areas for improvement.

While it may take time, a comprehensive review should include a timeline of the incident, response actions taken, and effectiveness. Additionally, all stakeholders involved in the incident response should be engaged to gather a holistic understanding.
Update Incident Response Plan
Revise the incident response plan based on lessons learned. Address any identified weaknesses and refine procedures to improve detection, response, and recovery capabilities. If applicable, implement preventive measures and ensure staff are trained on the updated procedures.
Additionally, regularly test the revised plan through simulations or tabletop exercises to confirm its effectiveness, ensuring the organization is better prepared to prevent and respond to future breaches.
Enhance Organizational Awareness
Use the incident as a learning opportunity to raise organizational awareness about cybersecurity. Share key findings and improvements from the post-incident review with all employees to reinforce the importance of security protocols, especially if the incident was enabled by social engineering or human error.
Provide updated training focused on the tactics used in the breach and the revised response procedures. This proactive communication fosters a security-focused culture and empowers staff to recognize and prevent potential threats.
Be Ready to Respond with Secure, Out-of-Band Event Management and Remediation
Your teams are the backbone of our organization’s security. Equipping them with the right tools and processes helps them manage a data breach more effectively, reducing its impact and expediting recovery.
It’s essential to have a well-defined incident response plan in place before a breach occurs. This proactive preparation can significantly improve your organization’s ability to handle and recover from data breaches.
Is your business ready to respond to a data breach or other disasters? We’ve compiled a disaster readiness checklist to help you understand your current processes and how to enhance resilience — download our Disaster Readiness Checklist today.
EWEBINAR
Experience the ShadowHQ platform
Walk through a cyber breach scenario in a 15 minute demo.
GUIDE DOWNLOAD
Disaster Readiness Checklist
When an emergency happens, every minute counts.


