Building an Effective Data Breach Response Team for Your Organization
Data breaches are a growing concern across all industries, and for good reason — they’re expensive and possibly an existential threat. The increasing data breach costs make defending against them required, not optional.
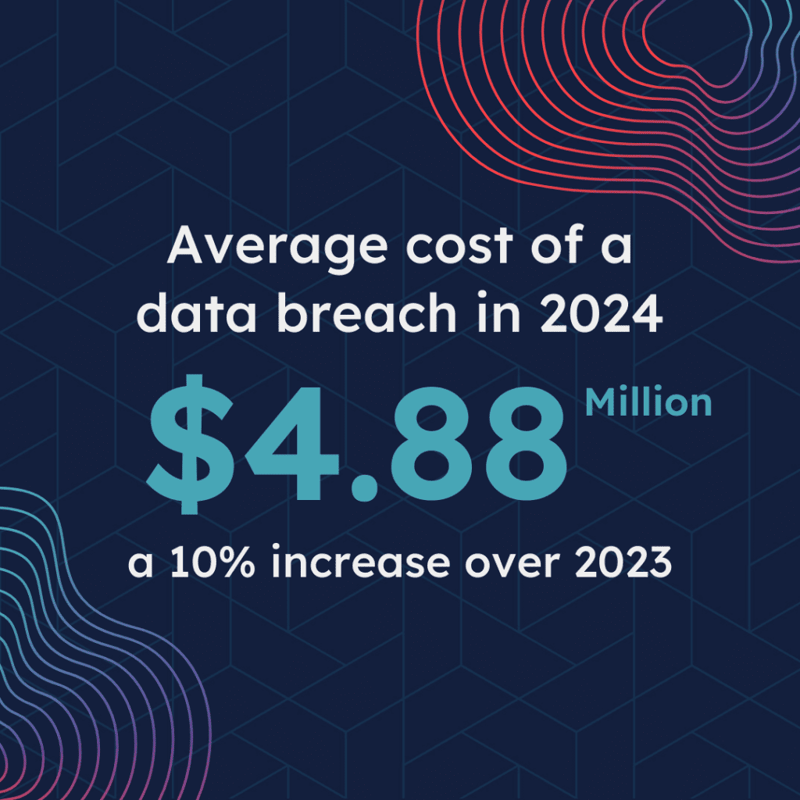
The latest IBM Cost of a Data Breach in 2024 report indicates that the average global cost of a breach is US $4.88 million, a 10% increase over 2023. The report also broke down how this cost is rising and the major contributors to it, and it gave recommendations for mitigating attacks and minimizing their costs.
Several moving pieces add up to this figure, including:
- Lost business
- Downtime
- Lost customers
- Cost of post-breach responses
- Paying higher regulatory fines
Working to prevent breaches is the first line of defense, but the second line of defense is a robust incident management response plan that takes a holistic approach to effectively containing and quickly recovering from breaches.
How might your incident response plan affect your real costs during and after a data breach? Let’s dive into this new report from IBM and unpack how it relates to your cyber incident response plans.
Related: 7 Practical Tips to Improve Your Cybersecurity Incident Response
1. Companies Take 292 Days to Identify and Contain Breaches Involving Stolen Credentials
An incident response plan involves being able to detect an incident. However, businesses take 292 days to identify and contain breaches involving stolen credentials. An attacker having almost a year of access to your systems is devastating and drives up the costs of a data breach.
It’s worth highlighting that compromised credentials are the most common attack vector for data breaches, used in 16% of successful attacks. This is slightly ahead of phishing attacks at 15%, which often enables similar attacks.
Defending against and identifying these attacks requires platforms that can analyze network traffic for anomalous behavior. Contextual authentication and zero-trust architecture can go far in preventing stolen credentials from enabling a breach.
However, your cybersecurity incident response plan must be updated and practiced to form your second line of defense. Developing and continually improving your response team significantly reduces containing breaches, while risk assessments and mitigation controls help identify them.
2. Lifecycle Affects Total Cost of a Breach
The faster an incident is contained, eradicated, and recovered, the better. IBM sought to put a number on the costs of a data breach that’s reflective of its lifecycle and found breaches that were:
- Under 200 days cost an average of $4.07 million
- Over 200 days cost an average of $4.95 million
Plenty of factors are involved in a shorter lifecycle, and incident response planning is a major way to reduce it. A well-crafted and practiced incident response plan prepares teams to tackle specific scenarios head-on, ready to execute the plan rather than create one on the fly.
Additionally, establishing protocols and processes for communicating during an incident is critical to mounting a rapid recovery. If telecoms are down or compromised by the attacker, it will be challenging to coordinate recovery efforts.
That’s why a cornerstone of your incident response playing needs to be protocols for backup communications, like ShadowHQ’s out-of-band communications that keep your teams working together in real time.
3. 70% of Businesses Indicate “Very Significant” Disruption Following a Breach
Most businesses indicated they experienced significant disruptions after a data breach, which was the highest category. These high-level breaches cost an average of $5.01 million, while low-level breaches cost $4.63 million.
While other areas of the report focused on mitigation and immediate responses, this area is concerned with the lasting effects of a breach. Once contained and eradicated, systems might be brought back online, but the total disruption can ripple throughout the business.
Why is there a lasting disruption? One reason why businesses are so disrupted is because modern business depends on data. If organizations need to make data unavailable while new controls are implemented, the entire organization can be brought to a crawl.
Early detection and rapid response are critical to having a less severe disruption once the incident is resolved. Minimize the impact and minimize the total expense.
4. Extensive Post-Breach Recovery Time
Out of all respondents who experienced a breach in 2024, only 12% indicated recovery was complete, while 88% said they were still working on recovery. Why does this take so long? Understanding what recovery means is important to see how it’s become such a major concern.
IBM defines full recovery as:
- Operations are back to normal in any areas impacted by the breach.
- All compliance obligations are met, including fines and corrective actions.
- Customer confidence is restored.
- New controls or technologies are in place to prevent future breaches.
You can see how technologies aren’t the entire picture, as rebuilding customer confidence might be a long-term goal.
Building and refining an incident response team is simply mission-critical to containing and recovering from a data breach. You’ll also need the right platforms to give your teams the necessary tools to defend against and respond to incidents, which in turn will reduce total costs.

5. Regulatory Fines are Rising
Alongside security, compliance has been at the top of organizations’ minds across all industries. A modern business faces more regulatory requirements than ever before, and many of these requirements focus on data — which may involve fines following a breach.
IBM found that 22.7% more organizations are paying over $50,000 in regulatory fines than last year, with a 19.5% increase in those paying more than $100,000. The report attributes this rise to the increase in the fines themselves.
Compliance requirements are in place to protect customers or even the general public, so they must be enforced. Fines are the primary enforcement action, and increasing these fines is intended to make it clear that compliance is a requirement and not optional.
When it comes to incident response planning, falling back to legacy methods for communicating and collaborating may lack the message logs or audit trails necessary when filing post-incident reports with regulatory agencies. This may result in much higher fines or other penalties, making it well worth investing in the right platforms that protect compliance in a crisis.
Minimize a Breach’s Cost with Effective Disaster Planning and Backup Communications
IBM’s report aims to take a macro-level approach to understand how much breaches are costing businesses, along with what factors increase or reduce these costs. We’ve broken down how many of the report’s findings and recommendations relate back to cyber incident response planning and disaster preparedness.
Failing to offer employee training, incident response planning, support for your incident response teams, and enabling security orchestration during a crisis can cost your organization $250,000 to $1 million for a single breach. Luckily, ShadowHQ supports all of these things in one centralized place, improving your response times and lowering the financial impact of a breach.
Taking action now can help significantly reduce your future costs should the first line of defense fail. One vital aspect of responding to any incident is communication — your teams need to collaborate on responses even if primary communications are compromised.
ShadowHQ offers an industry-leading out-of-band communication solution complete with file storage and message logging so you can stay in contact and compliant until the incident is contained.
Ready to take an important step towards reducing your costs of a breach? Book a demo today to learn more about how our platform’s secure bunker helps you rapidly respond to any scenario.


.png?width=600&height=331&name=Image%20(1).png)